|
The malware and IT security panorama has undergone a major change in terms of volume and sophistication. There has been an exponential increase in the number of viruses in circulation (around 200,000 new viruses appear every day), and new techniques for penetrating defenses and hiding malware are allowing threats to remain on corporate networks for long periods.
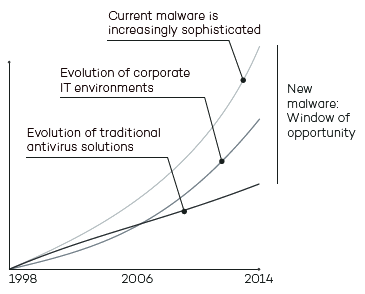
At the same time, IT environments have become increasingly complex, making management more difficult and systems more vulnerable.
Yet traditional antivirus solutions are out of step with the reality. Their linear evolution continues to use outdated detection techniques based on signature files and heuristic algorithms. This means that the results are inaccurate, i.e., that malware can go undetected and false positives are generated.
This discrepancy has led to what has been dubbed the ‘window of opportunity for malware’: the time lapse between the appearance of a new virus and the release of the antidote by security companies. An increasing gap that is exploited by hackers to get viruses, ransomware, Trojans and other types of malware into corporate networks. Such increasingly common threats can encrypt confidential documents and demand a ransom, or simply collect sensitive data for industrial espionage.
|
|
Governments, banks and other large companies are bearing the brunt of attacks that traditional antivirus solutions are simply not detecting in time. Our Research Department has analyzed millions of virus samples and the best antivirus products on the market to reveal that 18 percent of malware is undetected in the first 24 hours after it is released, and even after three months, these traditional solutions are still unable to detect 2 percent of malware.
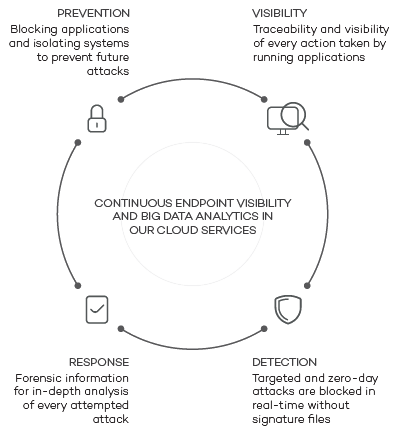
The solution to this situation is Adaptive Defense: a Panda Security service which can accurately classify every application running in your organization, only allowing legitimate programs to run.
To achieve this, we have been working for five years on a new security model based on three principles: continuous monitoring of applications on a company’s computers and servers, automatic classification using machine learning on our Big Data platform in the cloud, and finally, as an option, our technical experts analyze those applications that haven’t been classified automatically to be certain of the behavior of everything that is run on the company’s systems.
|